This week, there was a revelation that the Zoom teleconferencing software runs a localhost server on customer’s machines – and this localhost serve can be used to maliciously add your machine to conference calls (with the video active) by malicious websites.
About 2 years ago, I looked into how may websites make requests to localhost when the page loads. Let’s revisit the data to see how things have changed. I’ll use the HTTP Archive to look 5M webpages for references to localhost or 127.0.0.1:
select
requests.url request, requests.status, requests.respsize
from httparchive.summary_requests.2019_06_01_mobile requestswhere requests.url like “%//localhost%” OR requests.url like “%//127.0.0.1%”
There are a lot of pages that have a directory called localhost, so I force the search to only look for “//localhost” to remove these from the results.
Referencing Localhost
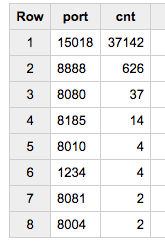
In the June crawl of 5M mobile websites there are 37,712 references to Localhost.
37,000 are coming from just one website:

The referrer is “InstallVestCert.html”, implying that this is attempting to load a certificate, and the file is appended with a random number between 0 and 1. As the page never stops loading, the HTTPArchive instance recording has ~37k failures before it errors out. The request is made to https://127.0.0.1:15018, which is a pretty funky port.
After this outlier, the remaining ports all appear to be regular HTTP ports often used in building sites locally (as I saw a year ago):
In general, requests to localhost (at least on root homepages) appear to be innocuous errors that can be easily fixed by resolving to the correct domain.